Aims and Objectives
Issues
Clock Synchronisation
Mutual Exclusion
Election Algorithms
Atomic Transactions
Implementing Transaction Processing: Two Methods
Committing Transactions
Concurrency Control
Deadlock
Each computer's internal clock can be different
No shared memory to synchronise on semaphores
Delay in data communications
Detecting computer/process crashes
When the processes are located on different computers
When processes on different computers require the same resource
Deadlock
relevant information can be anywhere on the system
processes can make decisions based only on local information
want to avoid having a centralised coordinator
no shared system clock
Logical Clocks

Physical Clocks
Atomic Clocks are used to keep accurate track of time. The National Institute of Standard Time broadcasts using the call sign WWV on SW Radio and computers can receive this (expensive)
Synchronising Physical Clocks
Time is not allowed to run backwards - client must "slow down" time if its clock is running fast
The time taken for the server to send the response and the client to receive it (and generate an interrupt, etc.) takes... a variable amount of time! Depends on network load, etc.
Client can ask server for time repeatedly and calculate average delay and take this into account when resetting its clock
What if you have no access to a WWV receiver?
A time daemon periodically asks all computers what time they think it is and computed the average time
Tells other computers the computed average time
A Token Ring Algorithm
if yes: enter critical section. On exit pass token to Process 1
if no: pass token to process 1
Bully Algorithm
The first process to notice sends an ELECTION message to all processes with ids higher than itself
If no process responds, the process wins the election and informs all processes that it is coordinator with immediate effect
If a process receives an ELECTION message is sends OK to the sender and holds and election
Eventually, all processes but one will have surrendered the election
The victor announces its victory
Atomic - either all steps in the transaction are completed, or none are
Consistent - the transaction does not violate system invariants (e.g., bank's law of conservation of money)
Isolated - concurrent transactions do not interfere with each other (the transactions are serialisable)
Durable - once a transaction commits, the changes are permanent
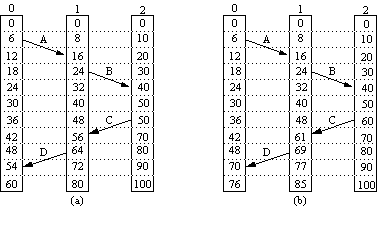
Private Workspace
Writeahead Log
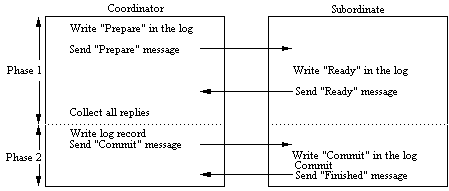
Two-phase Commit Protocol
Locking
Optimistic concurrency Control
Timestamps
Ostrich
Detection and Recovery
Prevention
Deadlock Detection and Recovery
Chandry-Misra-Haas (1987) algorithm is commonly used
Processes are allowed to request and wait on several resources simultaneously
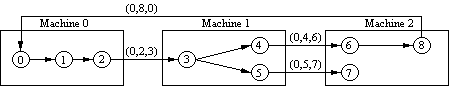
Algorithm invoked when a process is waiting on a resource
A probe message is sent to the process holding the resource
Message consists of blocked process number, process number of sender, process number of process holding the resource
Recipient checks if it is blocked waiting for a resource
If yes, updates message and forwards it
If message ultimately returns to first blocked process, deadlock exists
Deadlock Prevention
Processes are timestamped
If an older process wants a resource held by a younger process, wait
If a younger process wants a resource held by an older process, the younger process dies
... The wait-die algorithm